Many know Mozilla for their Firefox browser, and many software developers use their Mozilla Developer Network (MDN) for web technology documentation. However, many developers may not know that Mozilla has a tool called Observatory that allows you to scan your website’s security features and determine if you’re at risk for any common pitfalls.
What is Mozilla Observatory?
Mozilla Observatory is a website scanning tool that looks for server response headers, misconfigured TLS certifications, cross-site scripting vulnerabilities, and more! Each website is scored starting at 100, and each modifier will bring your website’s score down. There are even some modifiers that give you bonus points for a score greater than 100 (think of it as extra credit).
How can I use Mozilla Observatory to improve my website’s security?
First, we’ll start by navigating to the home page: https://observatory.mozilla.org/
You’ll notice that you have a couple of options, primarily privacy-related for those who may not want their website score publicly ranked or want their website exposed to 3rd party scanners. However, if you have a great website score, it can be great advertising to be on top of the High Achievers leaderboard.
All websites start with a baseline score of 100 and receive penalties or bonuses from there. The minimum score is 0, but there is no maximum score. Bonus points are only awarded if the site’s score without them is 90 (A) or greater. Currently, the highest possible score in the HTTP Observatory is 135.
Although both the letter grade ranges and modifiers are essentially arbitrary, they are based on feedback from industry professionals on how important passing or failing a given test is likely to be.
However, it does not test for outdated software versions, SQL injection vulnerabilities, vulnerable content management system plugins, improper password creation policies or storage procedures, and more. These are just as important as what the Observatory tests for, and site operators should not be neglectful of them simply because they score well on the Observatory.
HTTP Observatory Tab
Once you type your website in, your grade will be displayed to you. Underneath, you’ll find your Test Score modifiers, the things that brought your score down.
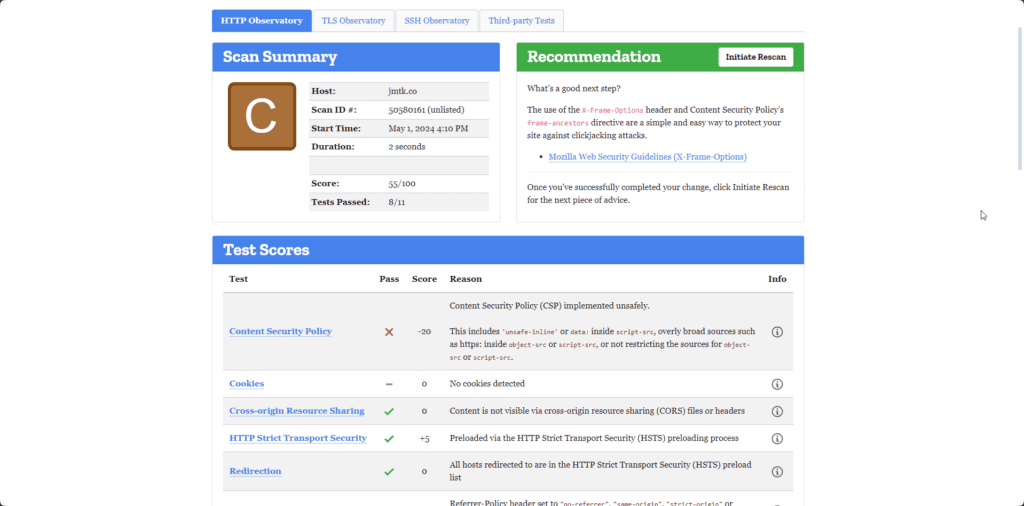
Your Content Security Policy can heavily affect the scores in this section. It is the successor to a lot of the cross-site scripting headers that allows you to fine-tune which websites you wish to allow to access your domain’s resources.
Your Content Security Policy can heavily affect the scores in this section. It is the successor to a lot of the cross-site scripting headers that allow you to fine-tune which websites you wish to allow to access your domain’s resources.
TLS Tab
This tab shouldn’t change too much, but it represents a plaintext view of your website’s TLS certificate. The most important thing under this tab that can affect your score is the TLS Cipher Suites. A Cipher Suite can vary between operating systems, each supporting different TLS cipher suites and priority order. The reason for an operating system supporting one cipher suite from another can depend on when it was released, the performance or size implications of supporting it, and whether it is considered “secure enough“.
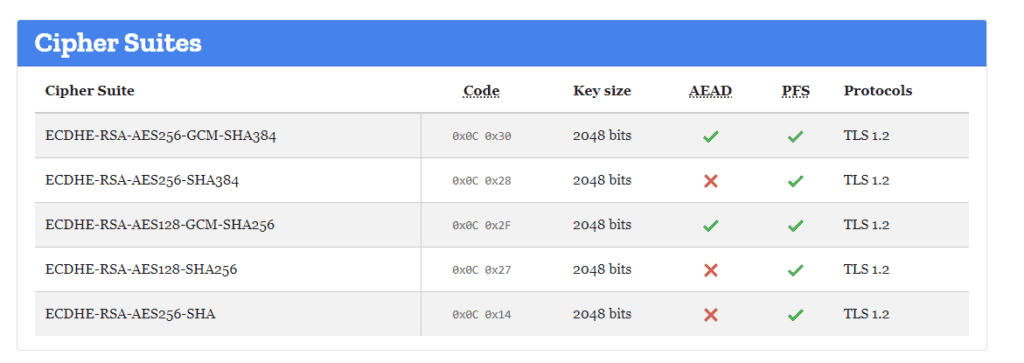
If you remove cipher suites, older clients such as Internet Explorer and cell phones may not be able to connect.
Third-party Tests Tab
The tests under this tab are a list of trusted website scanning tools that check for additional vulnerabilities, and cipher suites, and have their scoring systems to give you a better idea of where your site stands. My personal favorite is the SSLLabs tool which gives you a much more detailed explanation of each scanning point and why it gave you that score. It also gives you a list of devices that support each TLS cipher suite.
Now that I’ve improved scanned my website, what’s next?
After you fix your major scoring issues, your website is in a much better spot! However, it does not mean you have full immunity, there’s always more work to be done. For an added challenge, try tackling the OWASP Top 10.

